The iconic private eye of film noir would not get very far using traditional detective methods in the era of communicating by smart phones and the Internet, when there's no paper to leave a trail.
With current technology, a gumshoe need not even wear shoes, nor does an investigation necessarily require a professional investigator. Many options are available to anybody who wants to know what someone else is doing in the digital realm.
Keystroke loggers record everything that's typed on the designated computer or mobile device. They are installed as software such as Web Watcher, which leaves no visible files on the computer. In the case of Web Watcher, the program sends the information to a web-based account. It can report on email, social media, web history, searches, the computer's location, as well as the programs are being used, and the person monitoring the computer can set up alert words to trigger screenshots.
If the person installing that keystroke logging software needs to log in but doesn't have that computer's password, it's a matter of making another purchase: a password cracking utility.
(Read more: Former U.S. Spy Warns on Cybersecurity)
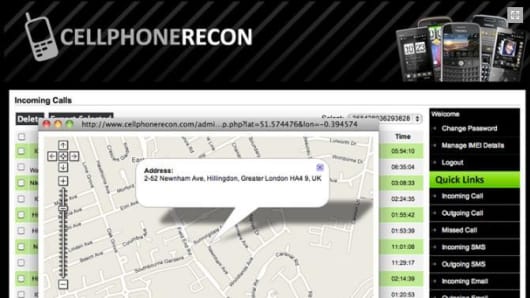
For smart phones, there are flash drives such as the Recover It that can pull deleted emails, videos, or pictures, search chat logs, or Cellphone Recon, which can show the user all phone calls made, GPS locations of the phone, text messages and emails, and Internet browsing history. Once installed, it's running whenever the phone is on, but the application does not show up on the mobile device as a running program.