The WannaCry ransomware cyber-attack that hit 300,000 victims in 150 countries recently was the talk of this week's huge information security (InfoSec) trade show in London, where 13,500 experts and 360 exhibitors gathered on June 6-8 to debate the latest threats and countermeasures in the on-going battle between cyber attackers and defenders.
WannaCry is a particular type of malicious software (malware) that locks files on a computer and demands payment to unlock them, hence its ransomware sub-set name. The Europol European police agency described the recent attack as "unprecedented" and retired U.S. Admiral and ex-NATO commander, James Stavridis, told CNBC it was a "pandemic" and very "worrisome."
Delegates at this week's InfoSec trade show in London talked to CNBC about what companies can do the protect themselves in future and the lessons that can be learnt from the WannaCry attack.
How to protect a financial institution (FI), "where the money lives" and to institute an effective cybersecurity policy at a new financial technology (fintech) disruptor such as Bristol-based robo-advisor Hargreaves Lansdown are also discussed in these expert interviews.
Adrian Asher, chief information security officer (CISO), London Stock Exchange (LSE) Group:
"The best way to fight WannaCry, or indeed any ransomware, is to do the basic protection methods well. Have a good upfront anti-virus system, then patching and back-up procedures in place. Beyond that you also need to think about the 'three lines of defense' model that has traditionally been used to mitigate risk."
"The Bank of England endorsed this 'three defensive lines' model last year in its Senior Managers Regime (SMR) update," continues Asher. "This requires risk responsibilities, including cyber risk, to be assigned to specific individuals within a clearly defined risk management structure."
The 'three lines' are:
- A primary function that owns and manages everyday risk. According to Asher this "would be the IT development team and information security (infosec) team at an FI working together" to ensure secure coding, good practice and that the basics are being followed.
- A secondary specialist supervisory risk management and/or compliance function that will check policy, oversee good practice and so on.
- Finally, a tertiary function needs to deliver internal and external auditing of procedures and provide independent oversight.
"It's important to have a multilayered, deep defensive posture and not to rely on a single perimeter approach," adds Asher. "This is the best way to protect your company."

In regard to the specific cybersecurity demands on a chief information security officer (CISO) at a large FI or financial market infrastructure (FMI) as the London Stock Exchange (LSE) Group is, Asher says that "unique regulatory and custodial duties rightly apply when you are looking after people's money". This can mean, however, that you are a natural target for criminals or nation state actors that want to disrupt a rival country because it is "where the money lives".
"It is good in some ways, however, because it means you always have the full support of the boardroom and cybersecurity is at the top of the agenda for FI directors and mentioned at every board meeting. This makes the job easier," says Asher, who was previously the CISO at Skype and other organizations where cybersecurity is of course mentioned but perhaps not supported as fully.
Jonathan Kidd, CISO, Hargreaves Lansdown:
"I agree that good patching and back-up procedures that you regularly test are important in the fight against WannaCry or any other malware," says fellow FI CISO Kidd of Bristol-based Hargreaves Lansdown, a fintech wealth manager that follows the robo-advisor model where machines suggest investments and manage accounts, rather than humans.
"Good data hygiene is also important and everyday practices like, for instance, ensuring all ports and nodes are closed so that there isn't a 'back door' easy way for ransomware to get into your systems. If you need to rely on your back-up facilities then you've gone wrong already."

"I should stress WannaCry didn't impact Hargreaves Lansdown and we were never at risk. A couple of days after the attack I had hundreds of our corporate clients checking to see if we'd been hit as part of their response procedure to check for any vulnerabilities in their financial supply chain. This is also good practice. I've been doing the same thing myself in the wake of the attack. Combine good practice like this, with doing the basics well and good threat intelligence, and your business should be safe."
Fintech cybersecurity
In regard to the role of an FI CISO, and if there are any differences between a fintech firm that wants to displace an incumbent financial services (FS) operator and established players, Kidd does admit there is a different threat landscape if you handle money.
"You're naturally a target," he says and this necessitates "stronger than usual IT, cyber and risk procedures to fight back about fraud or data attacks", which are frequent against any FI.
"Integrated systems that can share intelligence without being restricted by legacy IT that is siloed to particular departments, imprints or subject to any other restrictions is also important," says Kidd, in reference to how older large banks, wealth managers and other FIs that own several different brands under one umbrella often struggle to integrate alert systems across aging IT estates.
"This legacy problem isn't something fintechs suffer from," he says. "As a new start-up company that want to use technology to offer a better service at a cheaper operational running cost we get to choose a new technology stack that is agile, so it can scale up or down to meet demand and new additions can be more easily added in the future."
"We can also train our new employees in what good practice looks like from the get go. Retraining staff and encouraging good user behavior is always more difficult if you have to do it retrospectively."
Hargreaves Lansdown plans to open a new technology hub in Warsaw, Poland, this summer with 50 people who will work on IT development projects in conjunction with colleagues at the Bristol, U.K. headquarters. "I need to educate them in our agile development techniques where continuous innovation is demanded, alongside a requirement to practice safe coding, follow best practice and always think about cybersecurity in any new development, without slowing down its delivery," says Kidd.
He does admit that there is nothing to prevent good cybersecurity at an incumbent FI. Indeed most retail or investment banks, insurers or wealth managers have good cybersecurity because they are handling money. "A good security culture and boardroom backing are the key ingredients in protecting any firm, whatever its functions," he concludes.
Frank Downs, senior manager, cyber & information security, ISACA, an international trade body:
"I think you can learn lessons out of the reaction to WannaCry. There was a 'holier than thou' attitude from some companies that weren't caught out," says ISACA's Frank Downs. "Blame was almost placed on those affected because they simply didn't have good enough patching, data hygiene or back-up functions but that is wrong. People should be aware it may just have been a case of 'there but for the grace of god go I' and WannaCry could have hit them too."
"Some firms, especially if they have older systems, might have had to run a patch overnight when it first hit because they couldn't have downtime during the operational working day. Or perhaps they were caught out due to old legacy IT systems? This isn't a failure of the information security (infosec) professional charged with protecting the company or of procedures. It's an old IT problem." Responsibility sits with the Board.
Professor Angela Sasse, Director of U.K. Research Institute for the Science of Cyber Security:
The ISACA viewpoint that old technology can be the problem is something that Professor Sasse agrees with. As she said during a keynote session looking at user behavior at the InfoSec 2017 trade show conference stream in London on 6 June: "Half of all security problems are due to crap IT! Invest in new systems."
Speaking exclusively to CNBC afterwards, as the other interviewees did, Sasse added that her "key take-away from WannaCry was never to pay the ransom and always to back-up because at least then you can recover data, even if you do have to suffer disruption. No files are lost and it means you don't have to pay."
In addition to her role as Director of the U.K. Research Institute for the Science of Cyber Security (RISCS), which is funded by the National Cyber Security Centre (NCSC) that is part of GCHQ, the U.K. equivalent of America's NSA, Sasse is a Fellow of the U.K. Royal Academy of Engineering (FREng). She is also Professor of Human-Centred Technology in the Department of Computer Science at University College London (UCL). The latter day job is focused on examining user behavior and its crucial role in ensuring cyber security.
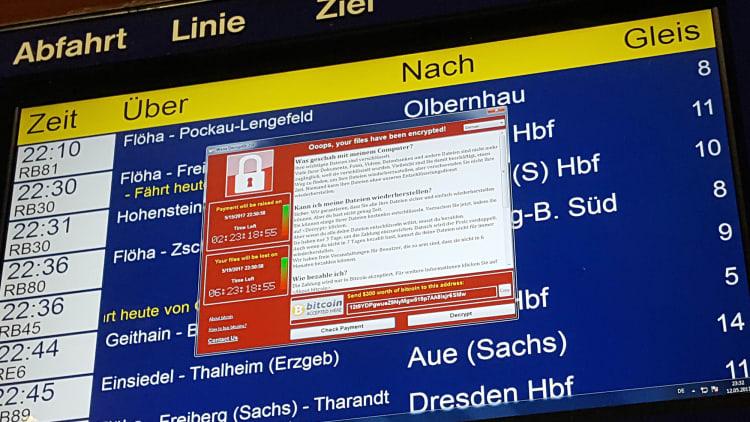
"I've spoken to a number of people and firms for my university-related research, who I cannot name, but they've jokingly referred to the good 'customer service' they received from ransomware attackers in the past. But you should never pay because that is never the end of it. Your details will end up on the dark web, shared around by cyber-criminals and the disruption will just continue on and on, so never pay. If you back-up you won't have to."
"In regard to the front-end, the requirement is to have effective malware protection and to invest in decent technology and education," she continued. "Business people in the Boardroom need to understand how investment decisions, or the lack of them, have knock-on impacts. It's the same for critical national infrastructures – look at the National Health Service (NHS) in the U.K., which was adversely affected by WannaCry due to historic underinvestment. You have to keep investing."
Sage advice there from CNBC's impromptu panel of cybersecurity experts. If you follow the above tips then hopefully you won't feel like crying and can protect your business in the future.

