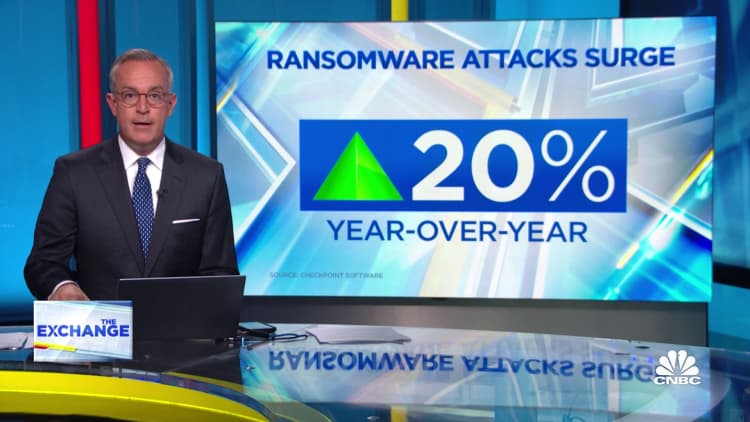
Companies are increasingly facing cybersecurity threats and data privacy regulations, ranging from how to handle artificial intelligence and large language models like ChatGPT to fears of hacking from espionage groups and bad actors. But the executive that many companies have in place to oversee these challenges, typically the chief information security officer, often does not have a backup.
Approximately 41% of companies do not have a succession plan for their CISO, according to a report from executive recruiting firm Heidrick & Struggles. Its data indicates that roughly three-quarters of CISOs said they were very or entirely open to changing companies in the next three years, underscoring the importance of succession planning and an increased focus on retention strategies.
"We consider not having a CISO succession plan to be a serious material risk that companies can easily mitigate," said Matt Aiello, partner and global cybersecurity practice leader at Heidrick & Struggles. The findings is highly concerning, he added, when considering how important cyber leadership is in today's business environment.
Risks of not having a cyber succession plan
The research also found that when organizations do have a succession plan it typically only includes one person, and that person is highly likely to be underqualified, Aiello said. That's because CISOs mostly hire "position players" on their teams, such as experts in security operations, application security, or compliance, not necessarily future leaders.
"Organizations that do not have a succession plan in place leave their business vulnerable to undue risk, as the threat landscape and regulatory environment continue to evolve at a rapid pace," Aiello said. "Should the CISO role wind up empty for any reason, the result could lead to serious business ramifications."
On top of that, the CISO role is particularly difficult to replace. "We find there are constraints with training and developing internal candidates in all of the necessary areas without sacrificing their day-to-day work," Aiello said. "This makes it easiest for organizations to source the next CISO externally. However, that process can still take significant resources — including time, money, and effort — given how limited the talent pool can be."
Without a clear succession plan for their cybersecurity leaders, organizations leave themselves exposed to significant cyber threats and risk, and are severely unprepared to navigate the fallout, Aiello said. "With the pace at which the marketplace and technology are evolving, leadership must consider the succession of their CISO as seriously as they consider that of their CEO," he said.
With a departure of a CISO, there is a loss of valuable institutional knowledge, which can impede an organization's ability to adapt to rapidly evolving cyber threats, said Daniel Soo, risk and financial advisory principal in cyber and strategic risk at consulting firm Deloitte.
"The lack of a successor could disrupt business-as-usual cybersecurity operations, resulting in delays, gaps in critical cyber risk management activities, and hindered cyber incident response and decision-making," Soo said.
In addition, CISO succession planning is key to ensuring that an organization has the right person at the right time to help drive the organization's cyber objectives, Soo said. "Lack of proper succession planning could result in disruption throughout an organization," he said.
This can include misalignment of resourcing potential, erosion of employee and stakeholder confidence, deterioration of organizational culture, and lost time toward achieving strategic objectives, Soo said.
How to develop a strong pipeline of potential CISOs
It's imperative for organizations to start succession planning as soon as a new CISO is in place, Soo said. "Planning should also involve leadership throughout the organization as well as the inclusion of the board," he said. "This can allow for thorough analyses of current priorities and risks, which can help set the foundation for the new CISO in several areas including talent and resources."
CISO succession planning should also involve anticipating future security requirements by considering the evolving nature of the business and technology landscape. "CISOs should analyze the security implications of these trends and develop policies, technologies, and skills to address future needs," he said. "Implementing a training program can help ensure that employees are equipped with the necessary skills to tackle upcoming security challenges."
A majority of CISOs think today's cyber risks will be different five years from now, according to the Heidrick & Struggles study. "This means the ideal successor should be defined in the context of what the CISO will need to do in the future — not what they do today," Aiello said. Selection committees should do their due diligence and analyze the talent pool both within and outside the organization, he added.
A critical part of any succession plan is building out a strong pipeline of potential successors to help safeguard the organization from risk, now, in the near term and in the long term. "In other words, preparing not only for this succession but many successions to come," Aiello said. "That requires a commitment to building out succession processes on a regular basis, including finding ongoing opportunities and pathways for the development of the internal cyber workforce."
In addition, organizations should maintain documentation outlining key responsibilities and tasks for each security function inclusive of the CISO, Soo said. "This can help organizations consider what the current and future responsibilities of the CISO role should and could look like," he said.